| CPC H04L 63/102 (2013.01) [G06F 3/067 (2013.01); G06F 3/0622 (2013.01); G06F 3/0664 (2013.01); G06F 9/45558 (2013.01); G06F 21/6245 (2013.01); H04L 9/0643 (2013.01); H04L 63/062 (2013.01); H04L 63/08 (2013.01); G06F 2009/45587 (2013.01)] | 20 Claims |
|
1. A computer-implemented method for secure data access control, comprising:
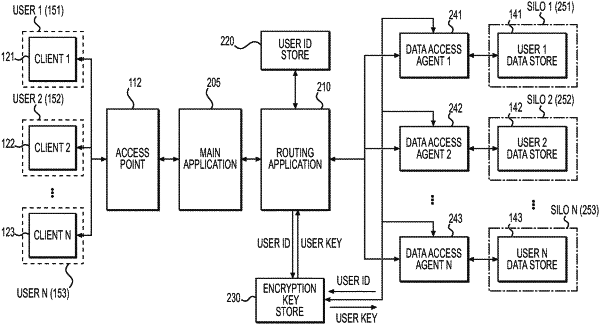
receiving, by a main application, a request to retrieve, store, or modify data in a data store from a client associated with a user;
based on the request, determining, by a routing application, an identifier of the user, wherein the routing application has an access account without permission to access the data store;
retrieving, by the routing application, an encryption key corresponding to the identifier of the user;
generating, by the routing application, a hash using a hash function of the encryption key;
based on the request and the hash, invoking, by the routing application, a data access agent corresponding to the identifier of the user, the data access agent having an access account with a set of permissions permitting the data access agent to access the data store and not permitting the data access agent to access data stores accessible to other data access agents;
retrieving, by the invoked data access agent, the encryption key using the identifier of the user;
generating, by the invoked data access agent, a new hash using the hash function of the encryption key;
verifying, by the invoked data access agent, the hash generated by the routing application based on a determination that the new hash is the same as the hash; and
accessing, by the invoked data access agent, the data store accessible to the invoked data access agent to perform the request.
|