| CPC H04L 63/029 (2013.01) [G06F 9/45558 (2013.01); G06F 2009/45587 (2013.01)] | 20 Claims |
|
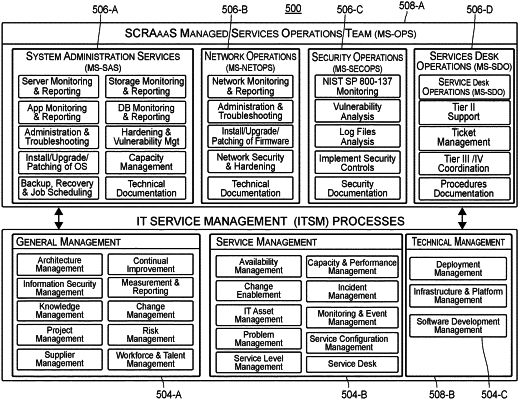
1. A computer-implemented method for providing continuous monitoring for a secure, classified remote access virtual desktop infrastructure to an end-user device, comprising:
processing, via one or more processors, input packets from a Commercial Solutions for Classified program and a virtual desktop infrastructure stack using via a routine, wherein the input packets include: (i) one or more event logs, (ii) network traffic, and (iii) system monitoring information, and wherein processing the input packets includes:
processing, via the one or more processors, the one or more event logs using a log forwarder,
processing, via the one or more processors, the network traffic using a packet indexing and capture tool, and
ingesting, via the one or more processors, the system monitoring information using one or more beats libraries;
generating, via the one or more processors, indexed logs based on event logs forwarded from an event forwarder, packets of the network traffic forwarded from the packet indexing and capture tool, and system monitoring information forwarded from the one or more beats libraries, using a log indexer;
generating, via the one or more processors, at least one of analytics or visualizations of the indexed logs; and
facilitating viewing of, via the one or more processors, the at least one of the analytics or the visualizations related to at least one of: (i) NetFlow, (ii) one or more applications, (iii) at least one of Application Performance Management or Network Performance Monitoring, (iv) security, (v) events, or (vi) logging.
|