| CPC H04L 9/3213 (2013.01) [H04L 9/088 (2013.01); H04L 9/3226 (2013.01); H04L 63/105 (2013.01); H04L 63/1433 (2013.01); H04L 67/306 (2013.01)] | 24 Claims |
|
1. A computer-implemented method comprising:
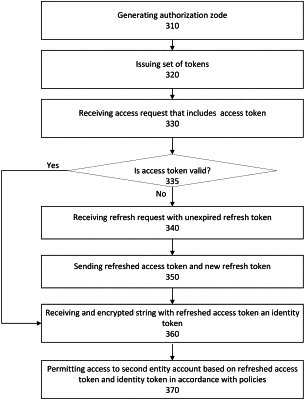
storing persistent login information in memory regarding a first service associated with login credentials for a first account of a user and a second service associated with different login credentials for a second account of the user, wherein the stored persistent login information includes a set of tokens that includes an access token, an associated refresh token, and an associated identity token;
generating an access request associated with a web application of the first service, wherein the access request includes the access token from the set of tokens and concerns access to the second account associated with the second service, wherein when the access request is received at a device associated with the second service, a determination is made as to whether the access token is valid;
tracking historical data regarding one or more risk factors;
applying artificial intelligence and machine learning to adjust one or more security measures in real-time based on a risk factor pattern detected in the historical data;
accessing data associated with the second account in real-time and in accordance with the one or more adjusted security measures, wherein the data is accessed based on the access token being validated before an end of an expiration period that is adjustable by the second service; and
populating a display of the web application of the first service with the data accessed in real-time from the second account.
|