| CPC H04L 9/0643 (2013.01) [H04L 9/0836 (2013.01); H04L 9/30 (2013.01); H04L 9/3247 (2013.01)] | 20 Claims |
|
1. A method comprising:
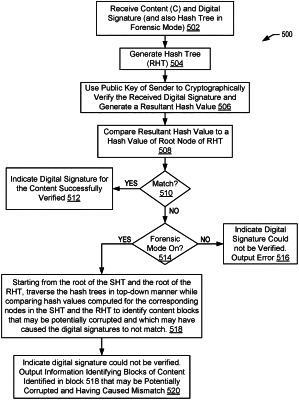
receiving at a recipient system from a sender system transmitted content (C) and appended content, the appended content comprising a digital signature associated with the content (C) and a hash tree (“SHT”) associated with the content (C) and comprising a plurality of first nodes and a first root node;
authenticating the digital signature based on a hash tree (“RHT”), wherein RHT is generated by the recipient system with content (C), wherein authenticating the digital signature based on RHT comprises comparing a resultant hash generated from the digital signature to a particular hash value generated based on at least a portion of RHT;
identifying a potentially corrupted portion of content (C) based on a comparison of at least portions of SHT with at least portions of RHT; and
indicating that the content (C) could not be verified.
|