| CPC G06Q 20/401 (2013.01) [G06Q 20/38215 (2013.01); H04L 9/0825 (2013.01); H04L 9/3213 (2013.01); H04L 9/3271 (2013.01); G06Q 2220/00 (2013.01); H04L 2209/56 (2013.01)] | 19 Claims |
|
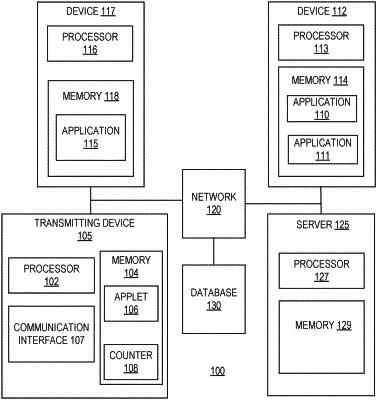
1. A contactless card with writeable access tokens, comprising:
a memory storing a key, an applet in communication with a first application stored on a mobile device, and transmission data comprising one or more identification credentials associated with the user;
a communication interface; and
one or more processors in communication with the applet stored in the memory and the communication interface, wherein the one or more processors are configured to:
execute the applet to create a cryptogram, using the key, wherein:
the cryptogram includes a request for an access token and the transmission data,
transmit the cryptogram to the first application running on the mobile device;
validate, by the first application, the transmission data included in the cryptogram;
generate, by the first application, the access token, upon successful validation of the transmission data, wherein the access token provides access credentials to a second system that is distinct from the contactless card and the mobile device associated with the user;
transmit, by the first application, an encrypted message to the card, wherein the encrypted message includes the access token;
decrypt, by the card, the access token using the key stored in the memory of the card;
store the access token in the memory of the contactless card, the access token being transmittable from the contactless card upon being queried by the second system; and
transmit, after entry of the communication interface into a communication field, the access token to a reader associated with the second system to which the user requires access.
|