| CPC G06F 21/577 (2013.01) [G06F 2221/033 (2013.01)] | 23 Claims |
|
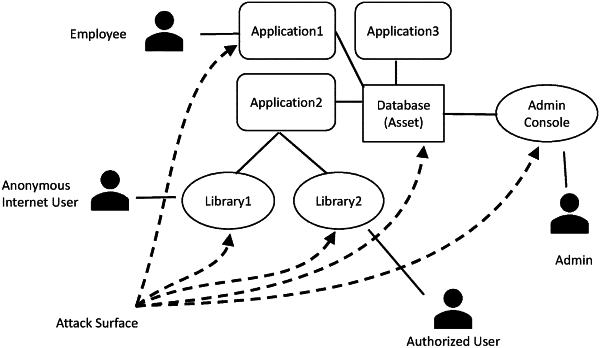
1. A computer-implemented method for analyzing software dependencies, comprising:
on a first asset, executing a technology agent configured to:
analyze software stored in memory of the first asset, the analysis comprising:
identifying nodes within the software,
recording a hierarchy of the nodes within the software,
identifying any dependencies within the software and with other portions of software; and
on the first asset, executing a security agent configured to:
analyze security of the software stored in the memory of the first asset, the security analysis comprising:
identifying security risks in the software and assigning a risk level to each,
associating each identified security risk with a node or edge, and
aggregating security risks at at least two different levels of the software hierarchy into hierarchy level risk scores by first applying weights to the risk levels and then adding the weighted risk levels of identified security risks associated with nodes or edges within the levels,
wherein:
the security analysis further comprises identifying a frequency of modifications made to each of a plurality of nodes, and
a modification frequency weight is applied that increases with a higher frequency of modifications identified for a particular node.
|