| CPC G06F 21/57 (2013.01) [G06F 12/1408 (2013.01); G06F 21/53 (2013.01); G06F 21/6218 (2013.01); G06F 21/71 (2013.01); G06F 21/79 (2013.01); H04L 9/0618 (2013.01); H04L 63/061 (2013.01); G06F 9/45558 (2013.01); G06F 2009/45587 (2013.01); G06F 2212/1052 (2013.01); G06F 2221/2107 (2013.01); G06F 2221/2149 (2013.01)] | 29 Claims |
|
1. A processing device comprising:
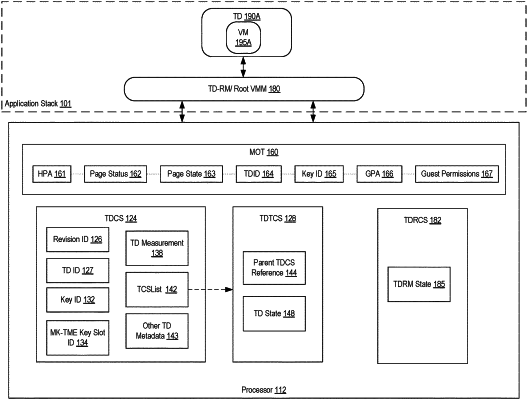
a memory ownership table (MOT) to store security attributes for a host physical memory page; and
a processing core that is to:
execute a trust domain resource manager (TDRM) to manage a trust domain (TD);
maintain a trust domain control structure (TDCS) for managing metadata of the TD, wherein the TDRM is to cause creation of the TD using an instruction, wherein the instruction specifies a region of physical memory for the TDCS as a parameter of the instruction, and wherein execution of the instruction generates an encryption key assigned to the TD and a key identifier (ID) and initializes a hash for a TD measurement in the TDCS, the key ID to be stored in the TDCS;
maintain an execution state of the TD in a trust domain thread control structure (TD-TCS) that is referenced by the TDCS and is access-controlled against software access from at least one of the TDRM, a virtual machine manager (VMM), or the other TDs; and
reference the MOT to obtain the key identifier (ID) corresponding to the encryption key assigned to the TD, the key ID to allow the processing device to decrypt memory pages assigned to the TD responsive to the processing device executing in the context of the TD, the memory pages assigned to the TD encrypted with the encryption key;
wherein the MOT security attributes comprise:
a TD identifier assigning the host physical memory page to the TD, and
an expected guest physical address used in the TD for the TDRM to perform memory mapping of the host physical memory page.
|