| CPC G06F 21/54 (2013.01) [G06F 21/74 (2013.01); G06N 20/00 (2019.01); G06F 7/582 (2013.01); G06F 7/588 (2013.01); G06F 16/245 (2019.01); G06F 21/577 (2013.01); G06F 2221/033 (2013.01); G06F 2221/2101 (2013.01); G06Q 50/265 (2013.01)] | 20 Claims |
|
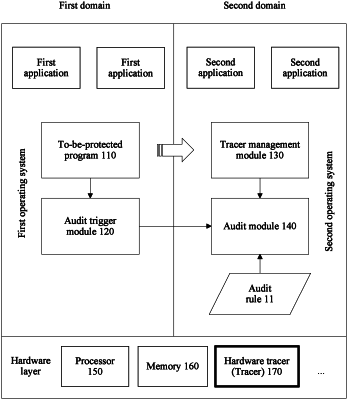
10. A security control method for a computer system in which a first domain and a second domain are deployed, the security control method comprising:
obtaining a process identification of a current process from the first domain before a tracer collects a to-be-audited information;
obtaining the to-be-audited information in the second domain using the tracer when a program in the first domain is executed, the to-be-audited information comprising control flow information of the program;
using the process identification together with the control flow information as the to-be-audited information;
searching the second domain for an audit rule that matches the process identification;
auditing, in the second domain, the to-be-audited information according to an audit rule; and
determining that the audit succeeds and allowing access to the second domain when the to-be-audited information matches the audit rule.
|