| CPC H04W 12/08 (2013.01) [G06N 20/10 (2019.01)] | 18 Claims |
|
1. An SVM (Support Vector Machines)-based secure access method for wireless terminals, comprising:
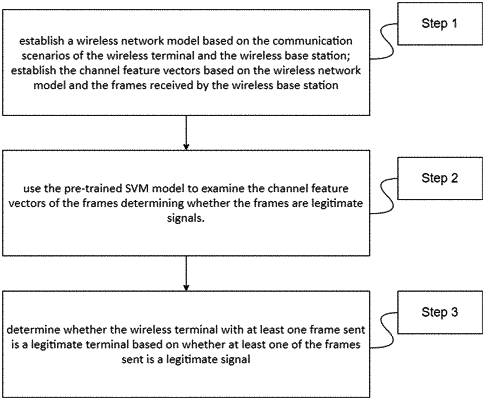
establishing a wireless network model based on the communication scenarios of a wireless power terminal and a wireless power base station;
establish the channel feature vectors based on the wire less network model and frames received by the wireless power base station;
extracting feature values of the feature vectors are one or more than one factors among the signal arrival moment, the signal angle, and the large-scale fading factor of the signal;
using a pre-trained SVM model to examine the channel feature vectors of the frames, determining whether the frames are legitimate signals, where the pre-trained SVM model is obtained from the extracted feature values of the signal based on the physical layer feature of a 5G communication system;
determining whether the wireless power terminal with at least one frame sent is a legitimate terminal based on whether at least one of the frames sent is a legitimate signal;
wherein the determination is achieved according to an SVM parameter combination optimization method based on improved differential evolution;
moreover, a method for obtaining each trial candidate composed of mutated candidate solutions in the improved differential evolution into perform two differential evolution mutations by combining a base of the random mutation operation and a base of the mutation operation for a best solution in current population, resulting in vj (g)=y−xr1(g)+(1−y)−xbest(g)+F−[xr2(g)−xr3(g)]+F [x14(g)−x1s(g)], where g is the current iteration number, i=1,2 - - - N, vt (g) is the trial candidate, y=, xr1(g) is a random candidate of the current population, xbest(g) is the best solution of the current population, best, r1, r2, r3, r4, r5 are candidates of the current population different from each other;
and authenticating the determined legitimate terminal to access the wireless power base station.
|