| CPC H04L 63/1425 (2013.01) [H04L 63/101 (2013.01); H04L 63/102 (2013.01); H04L 63/105 (2013.01); H04L 63/1433 (2013.01); H04L 63/1441 (2013.01)] | 20 Claims |
|
1. A method comprising:
for each operational technology (OT) network of a plurality of OT networks, said each OT network being a segmented network that is isolated from the Internet and comprising at least one physical process device and at least one control device configured to control the at least one physical process device:
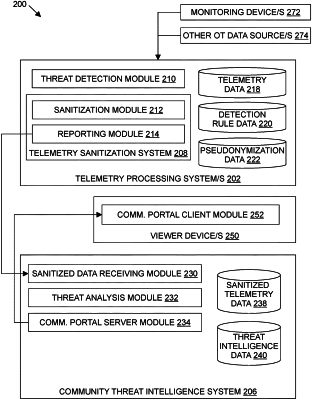
providing at least one monitoring device for deployment in said each OT network, the at least one monitoring device configured to process OT network traffic in an OT network protocol and collect telemetry data including telemetry data corresponding to the at least one physical process device and at least one control device, and
providing a telemetry sanitization system for said each OT network, the telemetry sanitization system configured to apply a sanitization process to the telemetry data collected by the at least one monitoring device to generate sanitized telemetry data that does not include sensitive data identifying said each OT network, any of the at least one process device, and any of the at least one control device;
receiving the sanitized telemetry data from the telemetry sanitization systems provided for the plurality of OT networks;
maintaining threat intelligence data generated based on the sanitized telemetry data, the threat intelligence data describing a plurality of security threats identified in the plurality of OT networks based on contextual data of the sanitized telemetry data, the threat intelligence data being insufficient to reidentify any OT network, any process device of a respective OT network, and any control device of a respective OT network; and
providing access to at least one of the threat intelligence data and the sanitized telemetry data to a plurality of users;
wherein receiving the sanitized telemetry data, maintaining the threat intelligence data, and providing access are performed by one or more computing devices.
|