| CPC H04L 63/1416 (2013.01) [H04L 51/08 (2013.01); H04L 51/42 (2022.05); H04L 63/20 (2013.01); H04L 67/306 (2013.01)] | 20 Claims |
|
1. A method comprising:
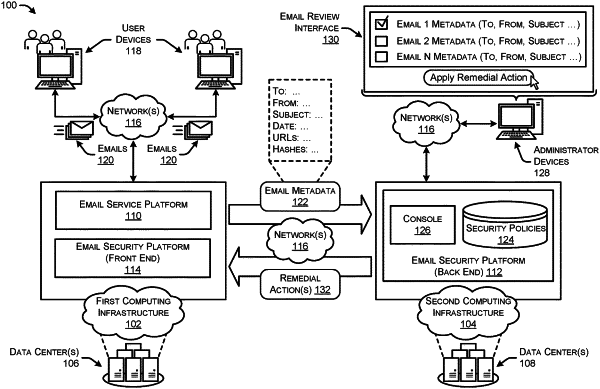
receiving, at a first cloud computing infrastructure that is managed by a first service provider and from a user device, an email for a user account registered with an email service, the first cloud computing infrastructure hosting the email service at a first physical location;
extracting, at the first cloud computing infrastructure, metadata from the email, the metadata comprising at least an email address from which the email was sent;
sending the metadata from the first cloud computing infrastructure and to a second cloud computing infrastructure that is managed by a second service provider, the second cloud computing infrastructure being different from the first cloud computing infrastructure and hosting an email security platform at a second physical location that is different from the first physical location;
evaluating, by the email security platform, the metadata against a security policy, the security policy defining malicious characteristics of emails;
generating, at the second cloud computing infrastructure, result data indicating a result of evaluating the metadata against the security policy;
storing, by the email security platform, the result data in a data store of the second cloud computing infrastructure;
providing an administrator account with access to a console for interacting with the email security platform;
receiving, via the console, a request from the administrator account to access the result data; and
providing the administrator account with access to the result data.
|