| CPC H04L 63/0236 (2013.01) [H04L 12/4633 (2013.01); H04L 63/029 (2013.01); H04L 63/0272 (2013.01); H04L 63/0485 (2013.01); H04L 67/10 (2013.01)] | 18 Claims |
|
1. A method, comprising:
receiving first traffic at a first traffic interface at a first compute server of a distributed cloud computing network, wherein the received first traffic is destined for a private application or service running on a server of a customer of a unified network service provided through the distributed cloud computing network, wherein the server is outside of the distributed cloud computing network, wherein the first traffic interface is an IPsec tunnel interface that interfaces with an IPsec tunnel from a router of the customer, wherein the IPsec tunnel interface is assigned an IP address that is an anycast IP address that is shared among the first compute server and a plurality of other compute servers of the distributed cloud computing network, and wherein a different one of the other compute servers of the distributed cloud computing network performed a handshake with the router including generating a set of one or more security associations for encrypting and decrypting;
receiving the generated set of one or more security associations for encrypting and decrypting traffic on the IPsec tunnel interface, wherein the received first traffic is encrypted;
decrypting the encrypted received first traffic using the set of one or more security associations;
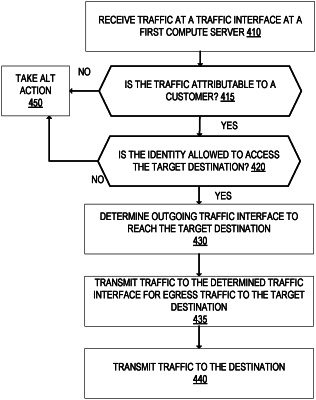
determining identity information associated with the received first traffic including that the received first traffic is attributable to the customer including identifying the customer based on the IPsec tunnel being associated with an account of the customer;
determining, using one or more policies configured for the customer and the determined identity information associated with the received first traffic, whether the received first traffic is allowed to be transmitted to the private application or service including determining whether traffic received over the IPsec tunnel is allowed to access the private application or service;
responsive to determining that the received first traffic is allowed to be transmitted to the private application or service, determining a second traffic interface that interfaces with the server of the customer, wherein the second traffic interface is a layer 7 traffic interface, and wherein the determined second traffic interface is on a second compute server of the distributed cloud computing network;
transmitting the received first traffic from the first compute server to the determined second traffic interface on the second compute server; and
transmitting, from the determined second traffic interface on the second compute server to the server of the customer, the received first traffic.
|