| CPC H04L 41/12 (2013.01) [H04L 63/062 (2013.01); H04L 63/065 (2013.01); H04L 63/0892 (2013.01)] | 20 Claims |
|
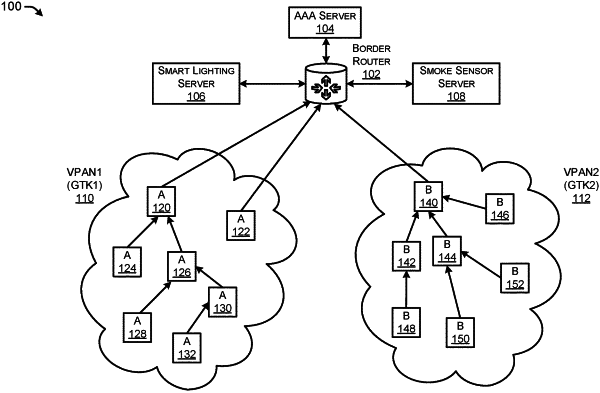
1. A border router comprising:
one or more processors; and
one or more non-transitory computer-readable media storing computer-executable instructions that, when executed by the one or more processors, cause the one or more processors to perform operations comprising:
receiving a first request to join a network from a first device;
authenticating the first device by communicating with an authentication, authorization, and accounting (AAA) server;
assigning a first sub-SSID (Service Set Identifier) to a first virtual personal area network (VPAN), wherein the first VPAN is associated with a SSID;
assigning, based at least in part on the first sub-SSID and in response to authenticating the first device, the first device to the first VPAN, wherein the first VPAN has an associated first group temporal key (GTK), wherein the first GTK is a temporary GTK that is valid for a limited time period and allows the first device to communicate with the second device during the limited time period;
distributing the first GTK to the first device;
receiving a second request to join the network from a second device;
assigning a second sub-S SID to a second VPAN, wherein the second VPAN is associated with the SSID;
assigning, based at least in part on the second sub-SSID, the second device to the second VPAN, wherein the second VPAN has an associated second GTK; and
distributing the second GTK to the second device.
|