| CPC H04L 9/3263 (2013.01) [H04L 9/088 (2013.01)] | 16 Claims |
|
1. A method, comprising:
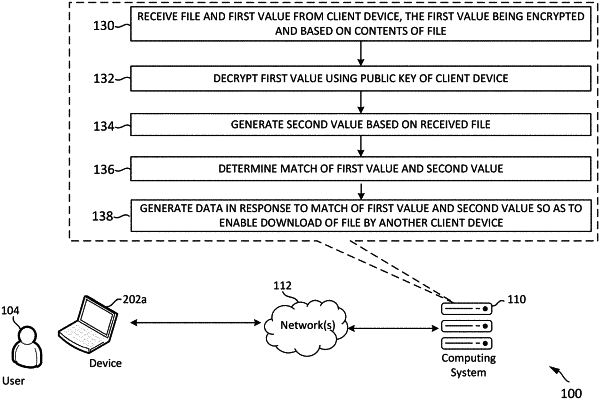
receiving, by a first client device, a file and data, the file having been previously uploaded by a second client device to a remote computing system and the data including a first hash value based on contents of the file previously uploaded by the second client device, the first hash value encrypted based on a document of the second client device;
determining, by the first client device, validity of the document of the second client device based on another document of the remote computing system;
decrypting, by the first client device, the first hash value with use of a key of the document of the second client device in response to validation of the document of the second client device;
determining, by the first client device, a second hash value for the received file, the second hash value based on contents of the file received by the first client device;
determining, by the first client device, validity of the received file based on a match of the first hash value and the second hash value;
receiving, at the first client device, an additional file and additional data, the additional file having been previously uploaded by the second client device to the remote computing system and the additional data including a third hash value encrypted based on the document of the second client device;
decrypting, by the first client device, the third hash value with use of the key of the document of the second client device in response to validation of the document of the second client device;
determining, by the first client device, a fourth hash value for the received additional file;
determining, by the first client device, that the received additional file is invalid based on a mismatch of the third hash value and the fourth hash value; and
denying access to the received additional file at the first client device.
|