| CPC H04L 9/3247 (2013.01) [G06F 21/32 (2013.01); G06F 21/44 (2013.01); H04L 9/3226 (2013.01); H04L 9/3297 (2013.01); H04L 63/083 (2013.01); H04L 63/0876 (2013.01)] | 14 Claims |
|
1. A system comprising:
a processor; and
a memory comprising instructions that are executable by the processor for causing the processor to:
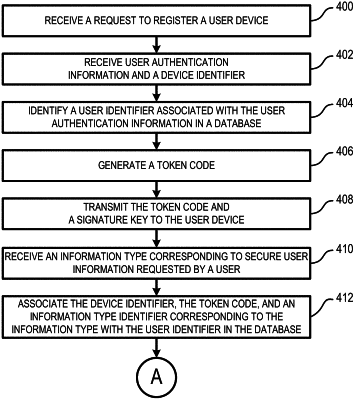
receive user authentication information from a user device;
authenticate the user device using the user authentication information;
based on authenticating the user device:
generate a token code,
determine a signature key,
transmit the token code and the signature key to the user device, and
associate a device identifier with the token code and the signature key in a database, wherein the device identifier corresponds to the user device;
subsequent to transmitting the signature key to the user device, receive a request for secure information from the user device, wherein the request includes:
the token code,
the device identifier corresponding to the user device,
and
an encrypted signature including a version of the device identifier and the token code encrypted by the user device using the signature key; and
subsequent to receiving the request:
generate a server-side signature that includes a version of the device identifier and the token code encrypted using a stored signature key retrieved from the database or another database;
compare the server-side signature to the encrypted signature in the request to determine a signature match; and
based on determining the signature match, authenticate the user device to access the secure information.
|