| CPC G06V 10/945 (2022.01) [G06F 1/3231 (2013.01); G06F 3/005 (2013.01); G06F 3/0482 (2013.01); G06F 3/0485 (2013.01); G06F 18/40 (2023.01); G06F 21/32 (2013.01); G06F 21/629 (2013.01); G06V 40/16 (2022.01); G06V 40/164 (2022.01); G06V 40/172 (2022.01); Y02D 10/00 (2018.01)] | 54 Claims |
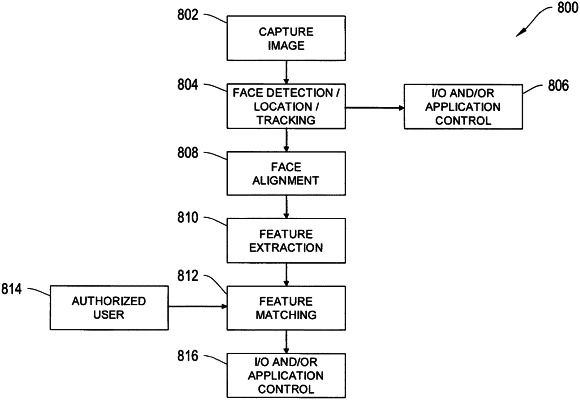
|
1. A method for controlling a computing system, the method comprising:
receiving, with the computing system, a communication from a second computing system;
in response to receiving the communication from the second computing system, evaluating, with the computing system, an environment of the computing system;
when the evaluating identifies existence of a person in the environment, initiating a first operation of the computing system that is related to the received communication from the second computing system; and
when the evaluating does not identify existence of a person in the environment, initiating a second operation of the computing system that is related to the received communication from the second computing system, wherein the second operation is different than the first operation.
|