| CPC G06F 21/577 (2013.01) [G06F 16/245 (2019.01); G06F 2221/033 (2013.01)] | 20 Claims |
|
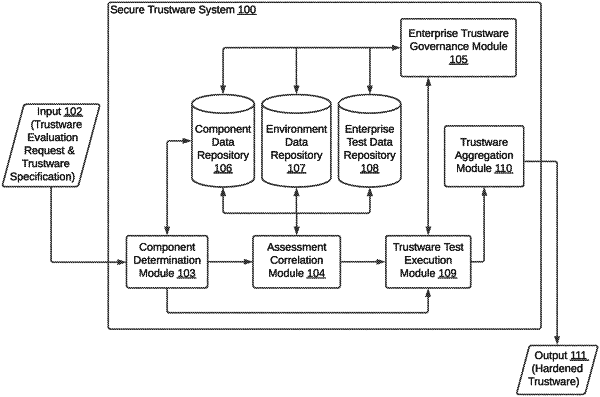
1. A method of managing security risk of information technology (IT) systems in an enterprise, the method comprising:
determining, by a secure trustware system, a set of valid trustware components that need to be evaluated for security risk of an IT system within an enterprise;
correlating, by the secure trustware system, information associated with each of the set of valid trustware components in a set of data repositories, wherein the set of data repositories comprises a trustware component data repository, an enterprise test case data repository, and a test environment data repository;
generating, by the secure trustware system, a mapping list comprising the set of valid trustware components, a set of test cases corresponding to each of the set of valid trustware components, and one or more test environments corresponding to each of the set of valid trustware components based on the correlation;
triggering, by the secure trustware system, a set of trustware security units for testing the set of valid trustware components, based on the mapping list and access control permissions received for the test environments that are being provisioned for the testing, wherein:
the testing comprises sequencing and prioritizing execution of the set of test cases so as to cover a testing scope of each of the set of valid trustware components and to cover a testing scope arising out of integrating each of the set of valid trustware components with each of the plurality of remaining valid trustware components, and
the set of trustware security units are arranged in at least one of a sequential manner or a parallel manner to align with execution of the set of test cases corresponding to each of the set of valid trustware components; and
identifying, by the secure trustware system, one or more security issues associated with the set of valid trustware components based on the testing.
|