| CPC G06F 21/575 (2013.01) [G06F 8/60 (2013.01); G06F 8/61 (2013.01); G06F 21/31 (2013.01); G06F 21/51 (2013.01); G06F 21/57 (2013.01); G06F 21/73 (2013.01); H04L 9/3247 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
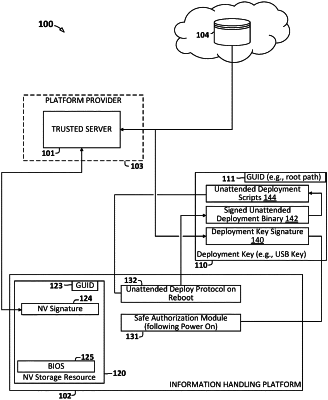
1. A method of deploying an information handling system, the method comprising:
responsive to detecting a power on signal, determining whether a key resource coupled to the information handling system is a deployment key for the information handling system, wherein said determining includes validating a globally unique identifier of the key resource against a deployment key signature, generated by a trusted server, stored on the key resource;
responsive to validating the key resource as the deployment key, performing a trust factor validation wherein the trust factor validation includes evaluating a trust factor for the deployment key against a second key, wherein the second key is bound to a nonvolatile storage component of the information handling system, wherein the nonvolatile storage component stores a second key signature, generated by the trusted server, based on a globally unique identifier (GUID) of the nonvolatile storage component;
responsive to validating the trust factor, rebooting the information handling system into an unattended deployment mode loaded from the deployment key;
validating an unattended deployment binary stored in the deployment key against the second key signature to establish a trusted execution session for loading one or more unattended deployment modules from the deployment key and deploying the information handling system by executing the one or more unattended deployment modules.
|