| CPC G06F 21/566 (2013.01) [G06F 9/544 (2013.01); G06F 21/552 (2013.01); G06F 21/565 (2013.01); H04L 63/145 (2013.01); H04L 63/1416 (2013.01); H04L 63/1441 (2013.01)] | 22 Claims |
|
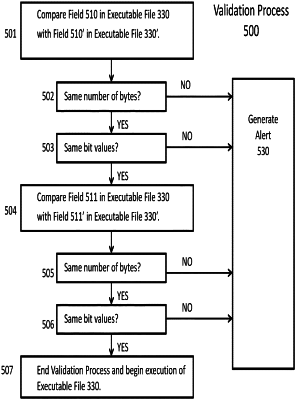
1. A method of validating an executable file to identify malware in a computing device comprising a processor, memory, non-volatile storage, an operating system, and a malicious code detection module, the method comprising:
identifying, by the malicious code detection module, a first executable file in the memory, the first executable file including: a first plurality of components that are not altered by the operating system when loaded into the memory;
identifying, by the malicious code detection module, a second executable file in the non-volatile storage, wherein the first executable file and the second executable file are associated with one another by the operating system;
determining that the second executable file has been compressed and/or encrypted using software packing;
determining whether the second executable file is capable of being unpacked;
unpacking the second executable file when the second executable file is capable of being unpacked;
comparing, by the malicious code detection module, a size of a first component of the first plurality of components of the first executable file and a size of a first component of a first plurality of components of the second executable file, wherein the comparing includes accounting for changes to the second executable file caused by the unpacking of the second executable file, and further wherein when the second executable file has not been compressed and/or encrypted using software packing, the changes need not be accounted for, and
generating an alert when the size of the first component of the first plurality of components of the first executable file and the size of the first component of the first plurality of components of the second executable file are different;
wherein the first component of the first plurality of components of the first executable file is less than the entirety of the first executable file and the first component of the first plurality of components of the second executable file is less than the entirety of the second executable file.
|