| CPC G06F 3/065 (2013.01) [G06F 3/067 (2013.01); G06F 3/0619 (2013.01)] | 20 Claims |
|
15. A computer system for a comprehensive backup solution, the computer program product comprising:
one or more computer processors;
one or more computer readable storage media, and program instructions stored on the one or more computer readable storage media for execution by at least one of the one or more computer processors, the program instructions comprising:
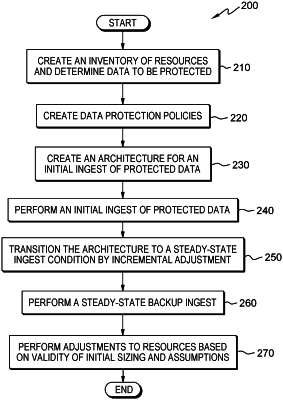
program instructions to create an inventory of resources associated with a computing environment requiring data protection by performing a backup operation including an estimate of future growth of the resources storing protected data;
program instructions to create a set of data retention policies, rules, and outcomes associated with the computing environment in conformance with predetermined business requirements;
program instructions to create an architecture for an initial ingest of protected data to backup storage, and an approach as to how the backup operation will be executed, based on the inventory of resources, a sizing and assumptions associated with determination of resources for the backup storage, and the set of data retention policies, the rules, and the outcomes associated with backup of the protected data;
program instructions to perform an initial ingest of the protected data to the backup storage;
program instructions to transition the architecture from a phase of the initial ingest to phase of a steady-state ingest, by incrementally adjusting the resources based on progress made from the initial ingest towards the steady-state;
responsive to completing the initial ingest of protected data, program instructions to perform a steady-state backup ingest;
program instructions to determine a validity of the sizing and assumptions associated with the resources for the backup storage; and
program instructions to perform an adjustment to the resources of the computing environment based on the determination of the validity of the sizing and assumptions.
|