| CPC H04W 12/06 (2013.01) [G06F 21/32 (2013.01); G10L 15/22 (2013.01); G10L 17/22 (2013.01); H04L 63/083 (2013.01); H04L 63/0861 (2013.01); G10L 2015/223 (2013.01); H04L 63/0853 (2013.01); H04L 63/102 (2013.01); H04W 12/63 (2021.01)] | 18 Claims |
|
1. One or more non-transitory computer-readable media storing computer-executable instructions, that when executed on one or more processors, causes the one or more processors to perform acts comprising:
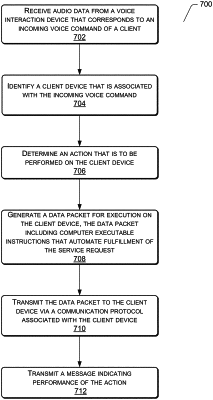
detecting, via a voice interaction device, an incoming voice communication from a client, the incoming voice communication including an implied request to perform at least one action that is associated with a computing resource;
parsing content of the incoming voice communication to identify the implied request to perform the at least one action;
identifying a client profile associated with the client based at least in part on the incoming voice communication, the client profile including a two-factor authentication protocol associated with the computing resource;
detecting a client device different from the voice interaction device;
determining a first authentication score based at least in part on an execution of a first factor of the two-factor authentication protocol at the client device;
transmitting, via the voice interaction device, a request for execution of a second factor of the two-factor authentication protocol;
determining a second authentication score based at least in part on the requested execution of the second factor of the two-factor authentication protocol at the voice interaction device; and
performing the at least one action that is associated with the incoming voice communication based at least in part on a combination of at least: (i) the first authentication score associated with the client device and (ii) the second authentication score associated with the voice interaction device, wherein:
the two-factor authentication protocol varies based on a particular type of access to a particular computing resources;
the second authentication score associated with the voice interaction device is based at least in part on a voice biometric; and
the first authentication score associated with the client device is independent of a voice biometric.
|