| CPC H04L 63/1425 (2013.01) [G06F 16/219 (2019.01); G06N 5/04 (2013.01); H04L 63/1416 (2013.01); G06N 20/00 (2019.01)] | 18 Claims |
|
1. A system for detecting anomalous user interactions with a computing resource, the system comprising:
a processor; and
a memory communicatively coupled to the processor and configured with instructions, which cause the processor to perform operations comprising:
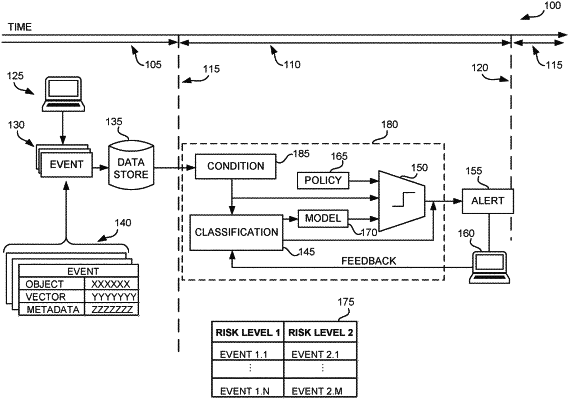
receiving a request to monitor interactions of a user with the computing resource, the interactions comprising causing the computing resource to execute an operation to access data objects hosted by a storage resource that is coupled to the computing resource;
obtaining first event data from the computing resource, the first event data comprising information that is indicative of first interactions of the user with the computing resource prior to receiving the request;
obtaining second event data from the computing resource, the second event data comprising information that is indicative of second interactions of the user with the computing resource after receiving the request;
identifying a security risk, the security risk based on analysis of past interactions of the user;
determining a metric based on the security risk of the user;
adjusting the metric based on an identified change in the security risk of the user;
determining, based on the first event data and the second event data, whether a deviation between the first interactions and the second interactions satisfies an indicated criteria, the indicated criteria including the metric determined based on the identified change in the security risk of the user; and
generating a security alert based on the determination.
|