| CPC H04L 63/061 (2013.01) [H04L 9/0643 (2013.01); H04L 63/0876 (2013.01); H04L 63/0884 (2013.01); H04L 9/50 (2022.05); H04L 2209/80 (2013.01)] | 12 Claims |
|
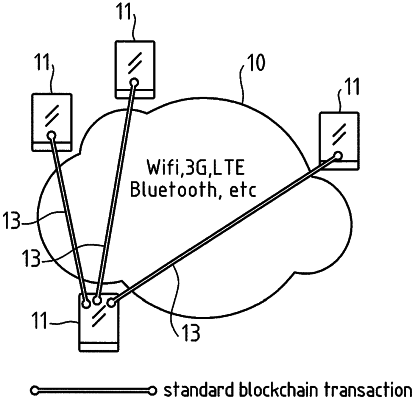
1. A device to be connected to a network where connected devices share a ledger of transactions between them under the form of a main blockchain composed of blocks, each block containing a timestamp and a link to a previous block, such device comprising:
at least one processor; and
at least one memory including computer program code;
the at least one memory and the computer program code configured to, with the at least one processor, cause the device at least to:
add forked chains extracted at the device to a main blockchain in order to build an enhanced blockchain and to store the enhanced blockchain in a chain database;
compute at least one Proof-of-Knowledge (PoK) chain based at least on the enhanced blockchain, a PoK chain being composed of PoK blocks, each PoK block containing a timestamp and a link to a previous PoK block,
store the PoK chain in a PoK database,
receive an authentication request from an application or a second device, the authentication request including at least one PoK,
retrieve, from the PoK database, at least one PoK chain corresponding to the application or the second device identified in the authentication request;
send the at least one PoK included in the authentication request and the at least one PoK chain retrieved from the PoK database to an authentication validator of the device,
compute at least one PoK based on the at least one PoK chain retrieved from the PoK database, compare it with the at least one PoK included in the authentication request, and if they match, validate the authentication request.
|