| CPC H04L 63/0236 (2013.01) [G06F 9/545 (2013.01); G06F 21/577 (2013.01); H04L 63/1425 (2013.01); H04L 63/166 (2013.01); H04L 63/20 (2013.01); G06F 21/552 (2013.01)] | 18 Claims |
|
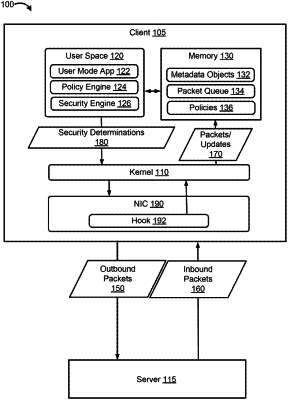
1. A method of network security, comprising:
receiving, by a kernel of a first machine, via a hook in a protocol stack of the first machine, one or more packets of a connection between the first machine and a second machine;
generating, by the kernel, a metadata object for the connection based on at least a subset of the one or more packets, the metadata object comprising an indicator of whether to capture packets of the connection into a queue;
adding, by the kernel, the one or more packets to the queue accessible by a security component of the first machine;
receiving, by the kernel, from the security component, a security determination regarding the connection based on the one or more packets added to the queue, wherein the metadata object is updated based on the security determination;
performing, by the kernel, an action with respect to the connection based on the security determination; and
determining, by the kernel, based on the indicator of the updated metadata object, whether to continue capturing additional packets of the connection in the queue.
|