| CPC G06F 9/4403 (2013.01) [G06F 9/45558 (2013.01); G06F 12/1009 (2013.01); G06F 21/78 (2013.01); H04L 9/30 (2013.01); H04L 9/32 (2013.01); G06F 2009/45579 (2013.01); G06F 2009/45583 (2013.01); G06F 2009/45591 (2013.01); G06F 2009/45595 (2013.01)] | 10 Claims |
|
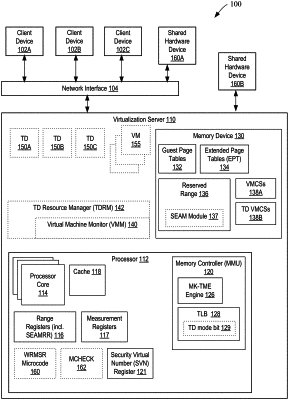
1. A processor comprising:
a range register to store information that identifies a reserved range of memory associated with a secure arbitration mode (SEAM) of the processor; and
a processor core coupled to the range register, wherein the processor core comprises security logic to unlock the range register on a logical processor, of the processor core, that is to initiate the SEAM; and
wherein the logical processor, via execution of the security logic, is to:
store, in the reserved range of the memory identified by the information stored in the range register, a SEAM module and a manifest associated with the SEAM module, wherein the SEAM module is to support execution of one or more trust domains;
initialize a SEAM virtual machine control structure (VMCS) within the reserved range of the memory, the SEAM VMCS to control state transitions between a virtual machine monitor (VMM) and the SEAM module; and
authenticate the SEAM module using a manifest signature of the manifest;
wherein the manifest comprises at least two of:
a manifest signers public key;
a first digest of the manifest signers public key, wherein the first digest is the identity of the SEAM module that is recorded;
a second digest of the SEAM module and associated loadable components; or
attributes of the SEAM module; and
wherein, to record a measurement of the SEAM module, the security logic is to:
generate a third digest of a combination of: (i) the SEAM module and associated loadable components; and (ii) the manifest signature; and
record, in at least one of a plurality of measurement registers, the third digest as the measurement of the SEAM module.
|