| CPC H04L 63/1466 (2013.01) [G01D 21/02 (2013.01); G01K 13/00 (2013.01); G05B 19/41885 (2013.01); G06F 16/2474 (2019.01); G06F 16/285 (2019.01); G06N 3/04 (2013.01); G05B 2219/32335 (2013.01)] | 20 Claims |
|
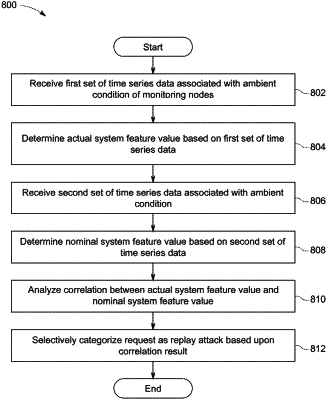
1. A method to identify a replay attack in an industrial control system of an industrial asset, comprising:
receiving a first set of time series data associated with an ambient condition of one or more first monitoring nodes at a first location within an enclosure of the industrial control system, the first set of time series data comprising first data values obtained during a particular time period;
determining an actual system feature value for the industrial asset based upon the first set of time series data;
receiving a second set of time series data indicative of the ambient condition at a second location external to the enclosure of the industrial control system, the second set of time series data comprising second data values obtained during the particular time period;
determining a nominal system feature value based upon the second set of time series data;
analyzing a correlation between the actual feature value and the nominal system feature value to determine a correlation result; and
selectively categorizing a request received by the industrial control system as a replay attack based upon the correlation result.
|