| CPC H04L 63/1441 (2013.01) [G06F 9/547 (2013.01); G06N 5/022 (2013.01); G06N 5/04 (2013.01); H04L 63/1416 (2013.01)] | 20 Claims |
|
1. A method for accelerating a remediation of a cybersecurity event, the method comprising:
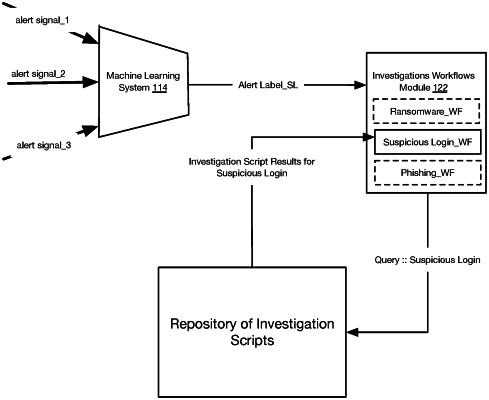
initializing an ensemble of automated investigation tasks based on detecting a cybersecurity event, wherein:
the ensemble of automated investigation tasks being defined by a subset of a plurality of distinct automated investigation tasks that is electronically linked to a likely cybersecurity event type associated with the cybersecurity event, and
obtaining a corpus of cybersecurity threat-probative data based on executing the ensemble of automated investigation tasks, wherein executing the ensemble of automated investigation tasks includes:
automatically sourcing one or more pieces of cybersecurity threat-probative data by one or more distinct automated investigative tasks of the ensemble of automated investigation tasks;
configuring threat response collateral based on the one or more pieces of cybersecurity threat-probative data, wherein the threat response collateral informs one or more threat mitigation responses to the cybersecurity event or informs a de-escalation response to the cybersecurity event; and
computing a cybersecurity threat severity value associated with the cybersecurity event based on extracting selective pieces of data from the one or more pieces of cybersecurity threat-probative data, wherein:
the cybersecurity threat severity value informs a routing of the cybersecurity event to one of a plurality of distinct threat mitigation or threat disposal routes.
|