| CPC G06F 21/602 (2013.01) [G06F 9/4401 (2013.01); G06F 12/1408 (2013.01); G06F 21/51 (2013.01); G06F 21/567 (2013.01); G06F 21/57 (2013.01); G06F 21/575 (2013.01); G06F 21/64 (2013.01); G06F 21/79 (2013.01); H04L 9/3242 (2013.01); G06F 2212/1052 (2013.01); G06F 2221/03 (2013.01)] | 14 Claims |
|
1. A cryptography module for a computing device, the cryptography module configured to:
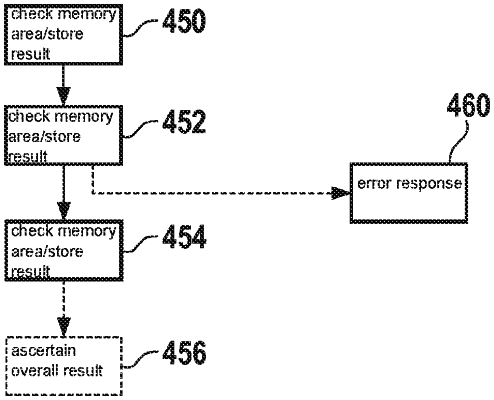
perform a check operation that produces a result, the checking operation checking at least one memory area of a memory device which is accessible by the computing device; and
store the result at least temporarily, wherein the result indicates whether a change has occurred in a content of the at least one memory area on account of a manipulation or an error, and wherein the cryptography module checks multiple memory areas of the memory device, the cryptography module checking the multiple memory areas at least occasionally in a random or pseudorandom sequence, and wherein the cryptography module is configured to carry out the check of the at least one memory area using a cypher-based message authentication code (CMAC).
|