| CPC H04W 12/068 (2021.01) [H04W 60/00 (2013.01)] | 20 Claims |
|
1. A method, comprising:
at an authentication server function (AUSF):
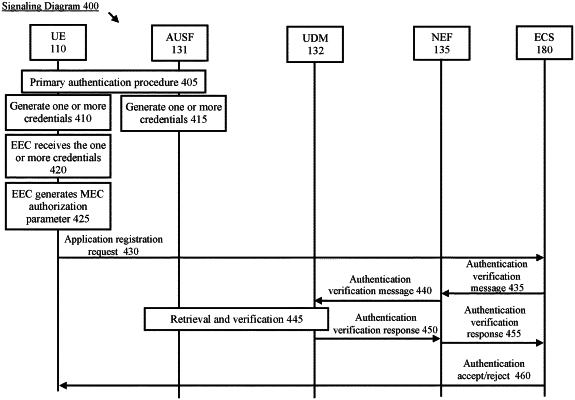
generating a first credential based on a second credential, the second credential generated for a procedure between a user equipment (UE) and a cellular network corresponding to the AUSF;
receiving an identifier associated with the first credential from a network exposure function (NEF) in response to the UE transmitting an application registration request to a server associated with an edge data network;
retrieving the first credential based on the identifier;
receiving a multi-access edge computing (MEC) authorization parameter;
verifying the MEC authorization parameter; and
transmitting an authentication verification response to the NEF.
|