| CPC H04L 9/3213 (2013.01) [G06F 16/245 (2019.01); H04L 9/3268 (2013.01)] | 20 Claims |
|
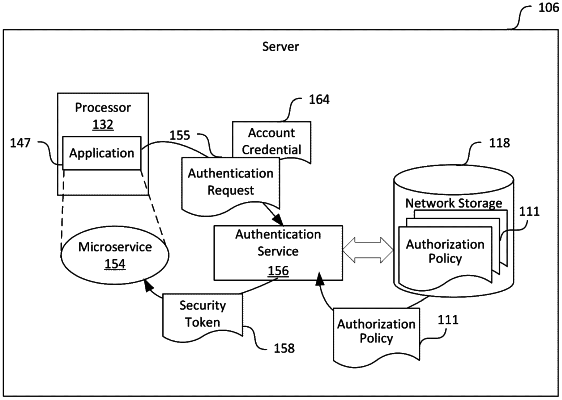
1. A computer-implemented method comprising:
receiving, at an authentication service, data representing a request for an identity assertion token corresponding to an application executed on a server;
in response to the request for the identity assertion token,
determining an application identity under which the application is executed to provide a computing service;
determining that the application with the application identity is authorized for the identity assertion token based on a first authorization policy record corresponding to the application identity; and
in response to determining that the application with the application identity is authorized for the identity assertion token, transmitting the identity assertion token to the server;
receiving, at the authentication service, data representing an authentication request from the computing service for a security token configured to authenticate the computing service to another computing service, the authentication request including the identity assertion token previously issued by the authentication service, wherein the identity assertion token comprises a digital data package that includes a security credential fear the application identity under which the application is executed to provide the computing service; and
in response to receiving the authentication request,
determining the application identity of the application based on the identity assertion token included in the authentication request; and
in response to determining that the application identity is authorized for the security token based on a second authorization policy record corresponding to the application identity, transmitting the sec u token to the computing service.
|