| CPC H04L 9/0841 (2013.01) [H04L 9/0825 (2013.01); H04L 9/0861 (2013.01); H04L 61/5007 (2022.05); H04L 2101/622 (2022.05)] | 15 Claims |
|
1. A method comprising:
receiving, via a memory controller of a memory device of a computing device from an application executing on a processor of the computing device wherein the processor and the memory device are communicatively coupled via a memory bus, a command to establish a communications session with a remote computing device communicatively connected to the computing device over a network, the command comprising a command to access a network supported by firmware of the memory controller;
generating, by the memory controller, a shared symmetric key, the shared symmetric key shared between the memory device and the remote computing device;
storing, by the memory controller, the shared symmetric key in a secure area of the memory device inaccessible by the processor of the computing device;
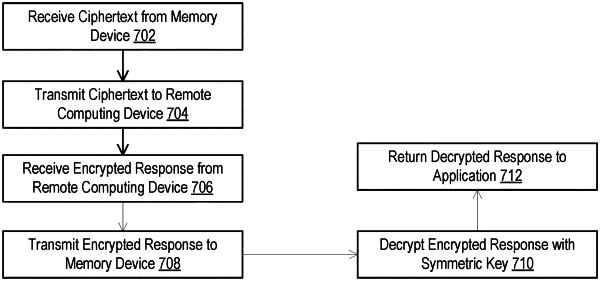
receiving, at the memory controller, a second command from the application, the second command including a network identifier of the remote computing device and a payload to transmit to the remote computing device;
retrieving, by the memory controller, the shared symmetric key from the secure area based on the network identifier;
generating, by the memory controller, a ciphertext by encrypting the payload using the shared symmetric key;
returning, by the memory controller, the ciphertext to the processor, causing the processor to transmit the ciphertext to the remote computing device;
receiving, by the memory controller, a third command from the processor including an encrypted response, the encrypted response generated by the remote computing device responsive to the ciphertext;
retrieving, by the memory controller, the shared symmetric key from the secure area based on the network identifier;
decrypting, by the memory controller, the encrypted response using the shared symmetric key to obtain a decrypted response; and
returning, by the memory controller, the decrypted response as a response to the third command.
|