| CPC H04L 63/20 (2013.01) [H04L 45/02 (2013.01); H04L 45/42 (2013.01); H04L 47/125 (2013.01); H04L 63/0236 (2013.01); H04L 63/029 (2013.01); H04L 63/0435 (2013.01)] | 18 Claims |
|
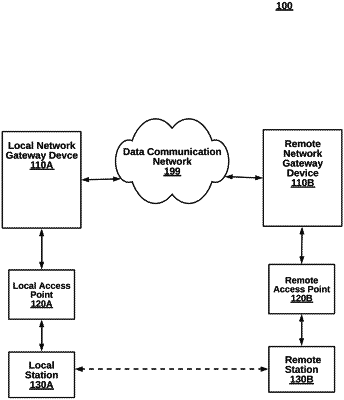
1. A local network gateway device having multiple processing blades coupled to a data communication network with a remote network gateway device and a local network with a plurality of stations, for session-aware load balancing of data packets across the multiple processing blades for the plurality of stations over an Internet Protocol security (IPsec) secure channel, network gateway device comprising:
a processor;
a network interface communicatively coupled to the processor and communicatively coupled to exchange data packets over the data communication network, wherein a first data packet of a specific session is received from the station as outbound traffic;
a plurality of security engine cards coupled through a common chassis, each security engine card performing firewall scanning, and the common chassis communicatively coupled with the processor;
a load balancing engine to assign a processing blade from the plurality of processing blades to scan data packets,
wherein the load balancing engine manages a session table and an IPsec routing table by updating the session table with a particular security engine card assigned to the session and by updating the IPsec routing table for storing a remote Internet Protocol (IP) address for a particular session, and
wherein outbound raw data packets of a particular session are parsed for matching cleartext tuple information prior to IPsec encryption, and inbound encrypted data packets of the particular session are parsed for matching cipher tuple information prior to IPsec decryption; and
a memory communicatively coupled to the processor and storing:
an Internet Key Exchange (IKE) control engine to send information about an IPsec tunnel to the load balancing engine including a remote gateway address and an IPsec tunnel key correlated with a source address and a destination address,
wherein the load balancing engine updates the session table and the IPsec routing table for handling subsequent data packets in the session,
wherein the network interface receives wherein an encryption engine on the assigned processing blade encrypts data packets from the session and transmits over an IPsec tunnel, and a decryption engine on the assigned processing blade receives data packets over the IPsec tunnel and decrypts data packets from the session and forwards to the station.
|