| CPC H04L 63/1425 (2013.01) [H04L 41/0681 (2013.01)] | 28 Claims |
|
1. A method, comprising:
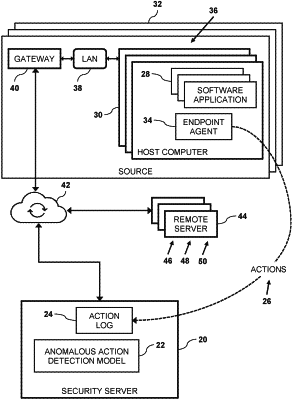
identifying multiple host computers executing respective instances of a specific software application, each given instance on each given host computer comprising a set of program instructions loaded, by the host computer, from a respective storage device;
collecting, from the host computers, information on actions performed by the executing instances, the information comprising action types and entities;
computing features based on the information collected from the multiple host computers;
comparing, by a processor, the collected information for a given instance to the features so as to classify the given instance as benign or suspicious; and
generating an alert for the given instance only upon classifying the given instance as suspicious,
wherein the host computers comprise first host computers that are distributed among a plurality of sources, and wherein a set of host computers distributed among the sources comprises the first host computers and additional host computers, and
further comprising normalizing the entities into normalized entities, and defining, for each one of the actions, a corresponding normalized action comprising the respective action type and normalized entity for the one of the actions.
|