| CPC G06Q 10/0631 (2013.01) [G06Q 10/105 (2013.01); H04L 63/20 (2013.01)] | 3 Claims |
|
1. A method for providing access to a computer system to execute a software test on the computer system in accordance with at least one constraint, said method comprising:
receiving, by a processor of the computer system, a request from a first individual within an organization for the first individual to access the computer system to execute the software test on the computer system;
in response to said receiving the request for the first individual to access the computer system to execute the software test on the computer system, said processor determining that the first individual has a specific role in the organization;
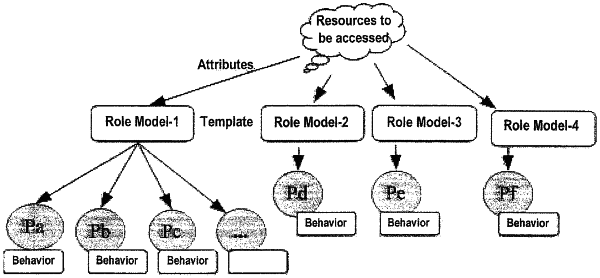
in response to said determining that the first individual has the specific role in the organization, said processor identifying a candidate entity repository corresponding to the specific role, wherein all individuals having the specific role in the organization are entries in the candidate entity repository;
said processor analyzing relationship network data, wherein the relationship network data includes a relationship weight between the first individual and each entry in the candidate entity repository, wherein each respective relationship weight denotes a strength of a relationship of the first individual with each entry in the candidate entity repository, wherein said analyzing comprises determining, for the first individual, valid entries from the entries in the candidate entity repository based on the relationship weight of each valid entry exceeding a preset relationship weight threshold, and wherein the valid entries in the candidate entity repository include a second individual and a third individual having the specific role in the organization;
in response to the second individual and the third individual having been determined to be valid entries in the candidate entity repository, said processor ascertaining a first constraint for accessing the computer system to execute the software test on the computer system by the first individual, based on a second constraint for accessing the computer system to execute the software test on the computer system by the second individual and the third individual, wherein the second and third individuals are permitted to access the computer system to execute the software test on the computer system in accordance with the second constraint, wherein the second constraint includes, during each month, only a first and second period of time throughout which the second and third individuals are respectively permitted to access the computer system to execute the software test on the computer system, and wherein the first and second periods of time have an overlapping period of time that is common to the first and second periods of time;
said processor aggregating the first and second periods of time, said aggregating comprising generating role model data that identifies the overlapping period of time, wherein the second constraint permits the second and third individuals to access the computer system to execute the software test on the computer system throughout the overlapping period of time, wherein the first period of time comprises a first interval of time not comprised by the second period of time, and wherein the second period of time comprises a second interval of time not comprised by the first period of time, wherein said ascertaining comprises ascertaining that the first constraint is that during each month the first individual is permitted to access the computer system to execute the software test on the computer system only during the overlapping period of time;
after said generating role model data that identifies the overlapping period of time, said processor providing, to the first individual from whom the request to access the computer system to execute the software test was received, the generated role model data that identifies the overlapping period of time, wherein said providing, to the first individual, the role model data that identifies the overlapping period of time and said analyzing relationship network data are performed concurrently;
said processor providing to the first individual access to the computer system to execute the software test on the computer system in accordance with the first constraint; and
said processor executing, as initiated by the first individual during said access to the computer system by the first individual, the software test on the computer system in accordance with the first constraint.
|