| CPC G06F 21/554 (2013.01) [G06F 2221/034 (2013.01)] | 13 Claims |
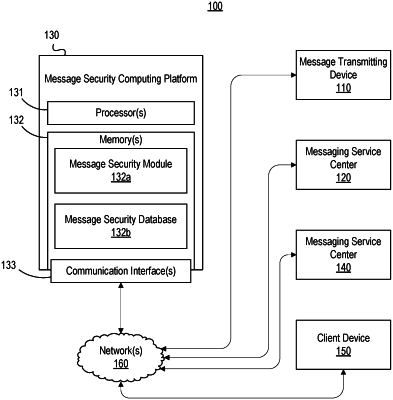
|
1. A computing platform, comprising:
at least one processor;
a communication interface communicatively coupled to the at least one processor; and
memory storing computer-readable instructions that, when executed by the at least one processor, cause the computing platform to:
receive, via the communication interface, a character-limited message sent to a user device;
scan the character-limited message to evaluate the character-limited message for suspicious content;
detect, based on the scan, that the character-limited message sent to the user device comprises suspicious content;
responsive to detecting that the character-limited message sent to the user device comprises the suspicious content, generate a modified character-limited message by selecting and inserting one or more unprintable characters into the character-limited message, wherein:
selecting and inserting the one or more unprintable characters into the character-limited message includes detecting a length of the character-limited message and inserting the one or more unprintable characters based on a number of available unused characters in the character-limited message,
the one or more unprintable characters are configured to track the character-limited message comprising the suspicious content and identify a confidence level, determined upon scanning the character-limited message, indicative of a confidence that the suspicious content is suspicious, and
the one or more unprintable characters include different unprintable characters indicating different confidence levels;
cause transmission of the modified character-limited message to the user device;
receive, via the communication interface, from the user device, a spam report confirming that the character-limited message comprises the suspicious content that is suspicious, wherein the spam report includes the modified character-limited message;
identify a presence of the one or more unprintable characters included in the modified character-limited message; and
adjust one or more filters based on identifying the presence of the one or more unprintable characters included in the modified character-limited message.
|