| CPC H04L 9/3236 (2013.01) [G06N 20/00 (2019.01); H04L 9/3271 (2013.01)] | 20 Claims |
|
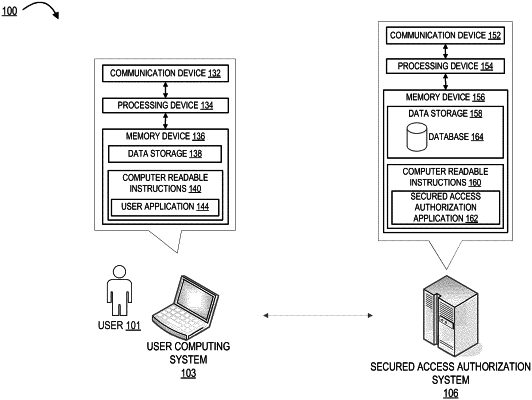
1. A system for authorizing secured access to perform a selected process on one or more networked systems, the system comprising:
a memory device with computer-readable program code stored thereon;
a communication device; and
a processing device operatively coupled to the memory device and the communication device, wherein the processing device is configured to execute the computer-readable program code to:
receive, from a user computing system, a request to execute the selected process on the one or more networked systems;
access a database of predefined processes determined to have a potential unacceptable impact on the one or more networked systems, where one or more of the predefined processes was added to the database if it is determined, based on continuously or periodically monitoring outcomes associated with operation of such one or more predefined processes on the one or more networked systems using machine learning, that such predefined process has a potential unacceptable impact on the one or more networked systems;
determine whether the selected process is listed in the database;
if so, prompt the user to complete an intent challenge;
based on detecting completion of the intent challenge, grant the request to execute the process;
generate a cryptographic hash based on the request to execute the process and the intent challenge; and
store the cryptographic hash in an integrity validation database.
|