| CPC H04L 63/1416 (2013.01) [G06F 16/2255 (2019.01); G06F 16/2379 (2019.01)] | 20 Claims |
|
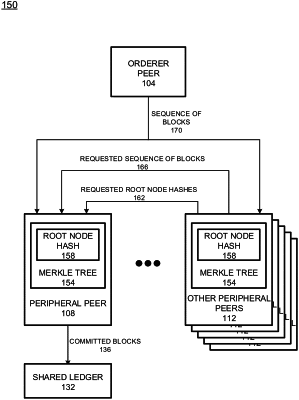
1. A blockchain network, comprising:
a peripheral peer node and a plurality of other peripheral peer nodes, wherein the peripheral peer node and each other peripheral nodes, of the plurality of peripheral peer nodes, are associated with a processor that when executing one or more instructions stored in a memory configures the processor to:
in parallel, receive a batch of new blocks from an orderer peer of the blockchain network, and
in parallel, calculate hashes of the batch of new blocks,
in parallel, generate a Merkle tree having leaf nodes that are the hashes of the new batch of blocks,
in parallel, generate a root node hash of the Merkle tree; and
wherein the processor associated with the peripheral peer node is further configured to:
request and receive root node hashes from a majority of other peripheral peer nodes of the plurality of other peripheral peer nodes,
identify the orderer peer as potentially malicious based on an identification that a rood node hash of the received root node hashes is different than the root node has calculated by the processor associated with the peripheral peer node,
in response to the identification of the orderer peer as potentially malicious, request a new block from another peripheral peer node, of the majority of peripheral peer nodes, corresponding to the different root node hash, and
in response to a receipt of the new block, verify the orderer peer as malicious when the new block is different than the new block received from the orderer peer by the peripheral peer node.
|