| CPC H04L 63/0245 (2013.01) [G06F 16/9017 (2019.01); H04L 47/2441 (2013.01); H04L 63/1425 (2013.01)] | 20 Claims |
|
1. A method comprising:
obtaining a first packet of an Internet Protocol packet flow at a security device;
providing the first packet to a firewall of the security device;
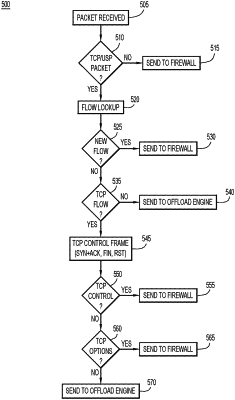
obtaining, at a classifier of the security device, an indication from the firewall that the Internet Protocol packet flow is to be split between a processing entity of the security device and the firewall of the security device such that non-control packets of the Internet Protocol packet flow are to be provided to the processing entity and control packets configured to indicate a change in a flow state of the Internet Protocol packet flow are to be provided to the firewall;
storing data at the security device that indicates that the non-control packets of the Internet Protocol packet flow are to be provided to the processing entity;
obtaining one or more non-control packets of the Internet Protocol packet flow at the classifier;
determining, by comparing at the classifier data contained in the one or more non-control packets of the Internet Protocol packet flow to the data stored at the security device, that the one or more non-control packets of the Internet Protocol packet flow are to be provided to the processing entity;
providing the one or more non-control packets of the Internet Protocol packet flow to the processing entity in response to the determining;
obtaining a control packet of the Internet Protocol packet flow at the classifier;
identifying a control flag in the control packet that indicates a potential change in the flow state of the Internet Protocol packet flow;
providing the control packet of the Internet Protocol packet flow to the firewall in response to identifying the control flag in the control packet;
obtaining at the classifier an indication from the firewall that non-control packets of the Internet Protocol packet flow should no longer be provided to the processing entity;
obtaining a non-control packet of the Internet Protocol packet flow at the classifier; and
providing the non-control packet of the Internet Protocol packet flow to the firewall.
|