| CPC G06F 3/0622 (2013.01) [G06F 3/0655 (2013.01); G06F 3/0679 (2013.01)] | 20 Claims |
|
1. A system for secure storage of sensitive data, the system comprising:
one or more processors; and
a memory in communication with the one or more processors, and storing instructions that when executed by the one or more processors are configured to cause the system to:
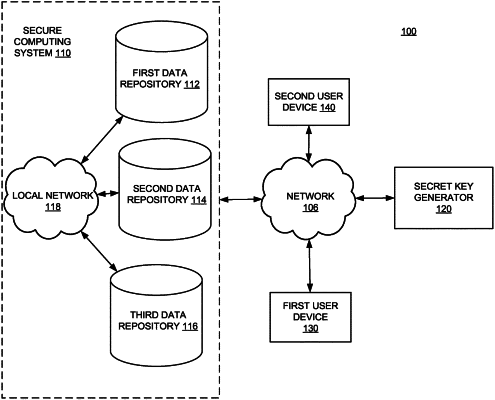
receive, at a first data repository, user data comprising a plurality of user names associated with a plurality of users, and a plurality of anonymized user identifiers;
receive, at a second data repository, user attribute data comprising a plurality of user attributes associated with one or more users of the plurality of users;
receive, at a third data repository, a first plurality of hash values uniquely identifying an association between each user attribute of the plurality of user attributes and one or more users of the plurality of users;
receive, from a first user device, a first request for a listing of user names associated with a first user attribute;
receive, based on a first user identifier associated with the first user device, a first secret key;
generate a second plurality of hash values, wherein each hash value of the second plurality of hash values is based on a combination of one of the plurality of anonymized user identifiers, one of the plurality of user attributes, and the first secret key;
determine a first subset of the first plurality of hash values that match the second plurality of hash values;
responsive to determining the first subset of the first plurality of hash values matching the second plurality of hash values, generate a first graphical user interface comprising the listing of user names associated with the first user attribute; and
transmit the first graphical user interface to the first user device.
|