| CPC G06F 21/6218 (2013.01) [H04L 63/1466 (2013.01); H04L 63/1491 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
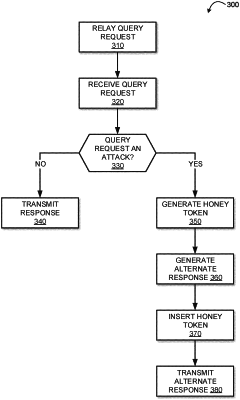
1. A computer-implemented method of implementing a dynamic virtual database honeypot, the computer-implemented method comprising:
relaying a query request received from a database client to a database;
receiving, from the database, a response relating to the query request;
determining the query request is an attack on the database based on session information relating to the database and the database client;
generating a honey token based on information contained within the response;
generating an alternate response formatted in a same format as the response and containing artificial information that masks the information contained within the response;
inserting the honey token into the alternate response that contains the masked information; and
transmitting the alternate response to the database client.
|