| CPC H04N 21/441 (2013.01) [H04N 21/235 (2013.01); H04N 21/26613 (2013.01); H04N 21/43856 (2013.01); H04N 21/4623 (2013.01)] | 20 Claims |
|
1. A method comprising:
at a headend including a non-transitory memory, a device key generator, a controller, and a transmitter:
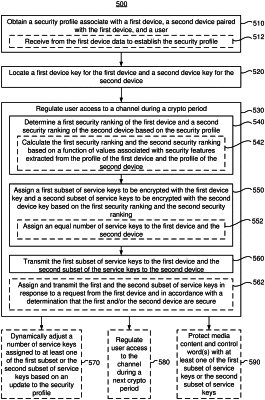
obtaining, from the non-transitory memory, a security profile associated with a first device, a second device paired with the first device, and a user;
locating, by the device key generator, a first device key for the first device and a second device key for the second device; and
regulating, by the controller, user access to a channel during an entitlement period, including:
determining a first security ranking of the first device and a second security ranking of the second device based on the security profile;
assigning a first subset of service keys to be encrypted with the first device key and a second subset of service keys to be encrypted with the second device key based on the first security ranking and the second security ranking;
generating a first subset of encrypted service keys by encrypting the first subset of service keys with the first device key and generating a second subset of encrypted service keys by encrypting the second subset of service keys with the second device key; and
causing the transmitter to transmit the first subset of encrypted service keys to the first device and the second subset of encrypted service keys to the second device.
|