| CPC H04M 1/67 (2013.01) [G10L 17/00 (2013.01); H04M 3/385 (2013.01); H04M 2201/41 (2013.01)] | 20 Claims |
|
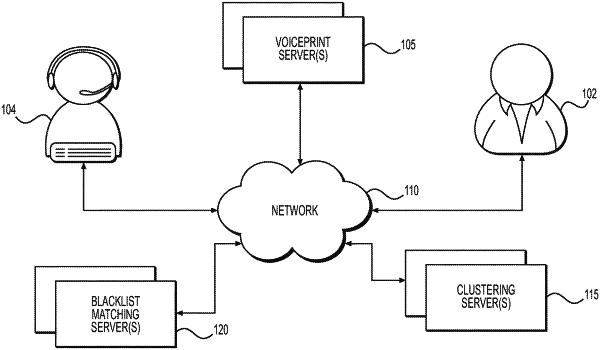
1. A computer-implemented method for identifying a voice associated with undesirable activity, comprising:
receiving an audio recording or audio stream associated with a voice;
determining a plurality of audio components of the audio recording or audio stream;
comparing the voice, using the determined plurality of audio components, with a library of voices, each voice in the library of voices defined by a cluster of audio recordings clustered together based on audio components of the audio recordings such that audio recordings associated with a same voice but different accounts are associated with a same cluster;
based on the comparing of the voice to the library of voices, identifying a cluster likely to correspond to a same voice as the voice associated with the received audio recording or audio stream;
determining, based on account information associated with the received audio recording or audio stream and metadata associating each audio recording in the identified cluster with a respective account, whether the voice associated with the identified cluster is associated with a plurality of accounts associated with different people; and
in response to determining that the identified cluster is associated with a plurality of accounts associated with different people, identifying the received audio recording or audio stream as associated with undesirable activity.
|