| CPC H04L 9/3247 (2013.01) [G06F 21/629 (2013.01); H04L 9/14 (2013.01); H04L 63/166 (2013.01)] | 19 Claims |
|
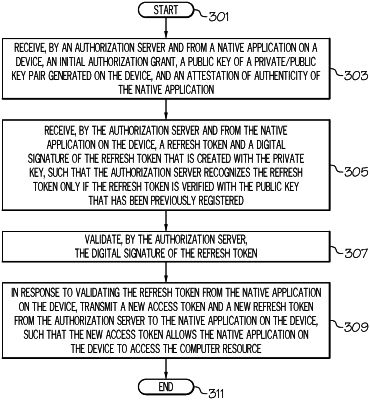
1. A method comprising:
receiving, by an authorization server and from a native application on a device, an initial authorization grant, a public key of a private/public key pair generated on the device, and an attestation of authenticity of the native application;
receiving, by the authorization server and from the native application on the device, a refresh token and a digital signature of the refresh token that is created with the private key, wherein the authorization server recognizes the refresh token only if the refresh token is verified with the public key that has been previously registered;
validating, by the authorization server, the digital signature of the refresh token;
in response to validating the refresh token from the native application on the device, transmitting, by the authorization server, a new access token and a new refresh token from the authorization server to the native application on the device, wherein the new access token allows the native application on the device to access the computer resource;
inputting, into a neural network, the initial authorization grant, the public key, the attestation of authenticity of the native application, the refresh token, and the digital signature of the refresh token, wherein the neural network is trained to generate a neural-network-generated access token and a neural-network-generated refresh token; and
comparing, by one or more processors, the new access token and the new refresh token that are generated by the authorization server to the neural-network-generated access token and the neural-network-generated refresh token in order to validate the new access token and new refresh token that is generated by the authorization server.
|