| CPC H04L 9/3247 (2013.01) [G06F 21/16 (2013.01); G06Q 50/184 (2013.01); H04L 9/0861 (2013.01); H04L 9/3236 (2013.01); H04L 9/3239 (2013.01); G06Q 2220/00 (2013.01); H04L 9/50 (2022.05)] | 20 Claims |
|
1. A method comprising:
receiving one or more proprietary files from a vendor;
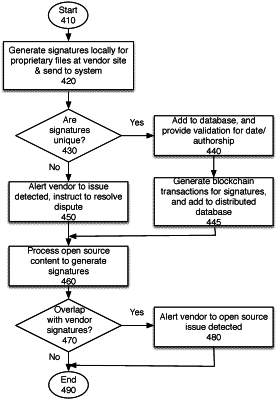
generating, by a signature generator embedded in one or more electronic design automation (EDA) tools, one or more signatures, wherein a signature corresponds to a segment of a proprietary file of the one or more proprietary files, wherein the proprietary file of the one or more proprietary files comprises hardware description language code;
validating each of the signatures to ensure that the signatures are owned by the vendor;
comparing a signature of the one or more signatures with existing signatures;
in response to determining that the signature is not unique and a conflict exists within the vendor based on the comparison, storing a relation between the signature and an existing signature, wherein the relation reflects an ownership relationship between the proprietary file and the vendor;
identifying, in response to determining that the signature is not unique, at least one of leakage, misappropriation, appropriation, or contamination of the one or more proprietary files with one or more of proprietary files from another vendor, and open source files.
|