| CPC H04L 9/0861 (2013.01) [H04L 9/0819 (2013.01); H04L 9/085 (2013.01); H04L 63/105 (2013.01); H04L 63/20 (2013.01)] | 17 Claims |
|
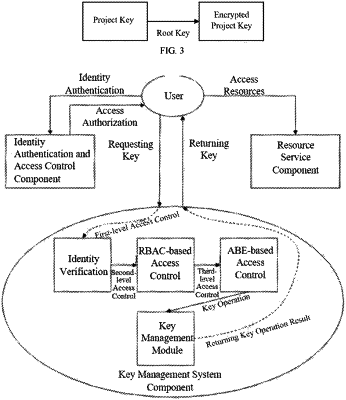
1. A key management method, comprising:
receiving key generation request information;
generating attribute access policy information on the basis of the key generation request information, wherein the attribute access policy information is an attribute set for encrypting a data key;
encrypting the data key on the basis of the attribute set for encrypting the data key;
receiving key acquisition request information;
on the basis of the attribute set for encrypting the data key, verifying whether attribute information of the key acquisition request information is included in the attribute set for encrypting the data key; and
in response to the attribute information of the key acquisition request information being included in the attribute set for encrypting the data key, acquiring a destination data key on the basis of the attribute information of the key acquisition request information;
wherein before the step of encrypting the data key on the basis of the attribute set for encrypting the data key, the method further comprises:
generating an initial data key according to the key generation request information;
generating a project key according to the key generation request information, wherein in response to the project key existing, the project key is used directly and encrypted with a system root key; and
encrypting the initial data key according to the project key to obtain a first encrypted data key.
|