| CPC H04L 9/0841 (2013.01) [H04L 9/006 (2013.01); H04L 9/0662 (2013.01); H04L 9/0825 (2013.01); H04L 9/085 (2013.01); H04L 9/14 (2013.01); H04L 9/3066 (2013.01)] | 9 Claims |
|
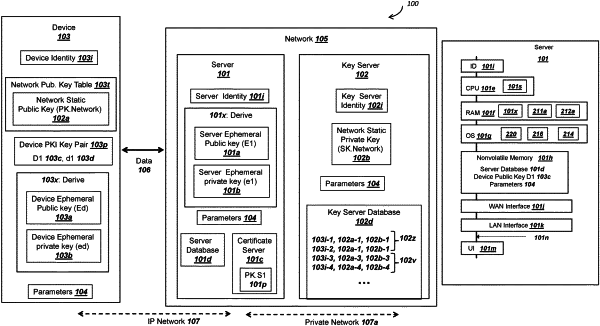
1. A method for a server to authenticate a device over a wireless network, the method performed by the server, the method comprising:
a) storing, in a memory, (i) a first point on an elliptic curve, and (ii) a shared key, wherein the shared key is stored by the device;
b) generating a value from a secure hash of at least the shared key;
c) selecting (i) a first integer as a first subset of the value and (ii) a second integer as a second subset of the value;
d) receiving, via a radio connected to the wireless network and from the device, a second point on the elliptic curve from the node, the second point comprising a public key for the device;
e) deriving a shared secret comprising an elliptic curve point addition of (i) the first integer multiplied by the public key for the device and (ii) the second integer multiplied by the first point;
f) deriving a symmetric ciphering key from a key derivation function with the shared secret;
g) receiving, via a radio connected to the wireless network and from the device, a ciphertext comprising (i) a device digital signature and (ii) a device certificate;
h) decrypting the ciphertext with the symmetric ciphering key in order to read the device digital signature and the device certificate; and
i) verifying the device digital signature using a device static public key from the device certificate.
|