| CPC H04L 9/0838 (2013.01) [H04L 9/008 (2013.01); H04L 9/0822 (2013.01)] | 20 Claims |
|
1. A method comprising:
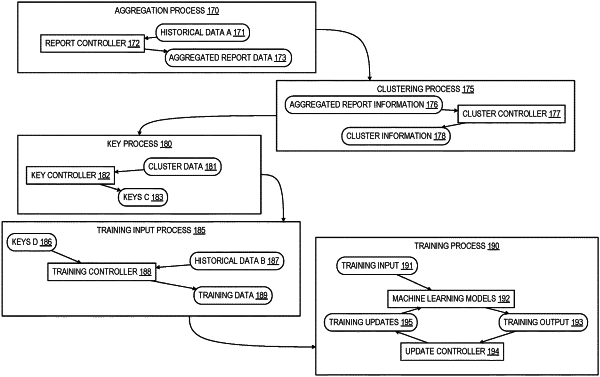
clustering a plurality of user devices into a plurality of groups of user devices, wherein each of the plurality of groups of user devices are assigned to use a corresponding group specific model in a plurality of group specific models;
transmitting a plurality of user encryption keys to use the group specific models to the plurality of user devices, wherein each user receives a corresponding user encryption key for a corresponding group specific model assigned to the each user;
receiving a plurality of encrypted transaction vectors from a plurality of user devices, wherein a corresponding encrypted transaction vector in the plurality of encrypted transaction vectors is encrypted using a corresponding group encryption key in the plurality of user encryption keys;
assigning the plurality of encrypted transaction vectors to ones of the group specific models such that any one group specific model is assigned those of the plurality of encrypted transaction vectors that share a common corresponding user encryption key in the plurality of user encryption keys;
generating, using the plurality of group specific models, a plurality of encrypted category vectors from the plurality of encrypted transaction vectors, wherein each of the plurality of encrypted category vectors comprises a corresponding encrypted recommended category for a corresponding encrypted transaction vector in the plurality of encrypted transaction vectors, and wherein each of the encrypted category vectors is generated by a corresponding one of the plurality of group specific models; and
transmitting the plurality of encrypted category vectors to the plurality of user devices for decryption by the plurality of user devices using a plurality of decryption keys corresponding to the plurality of user encryption keys.
|