| CPC H04L 9/0825 (2013.01) [H04L 9/0861 (2013.01); H04L 9/0894 (2013.01); H04L 9/14 (2013.01); H04L 67/1097 (2013.01)] | 18 Claims |
|
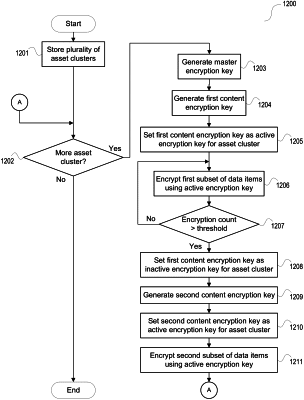
1. A computer-implemented method comprising:
storing, using a data store, a plurality of asset clusters, each asset cluster comprising a plurality of data items and associated with an active encryption key; and
for each asset cluster in the plurality of asset clusters:
generating a master encryption key;
generating, based on the master encryption key for the asset cluster, a first content encryption key;
setting the first content encryption key associated with the asset cluster as the active encryption key for the asset cluster;
encrypting a first subset of the plurality of data items of the asset cluster using the active encryption key and maintaining a count of a number of data items encrypted using the active encryption key;
determining the number of data items encrypted using the active encryption key exceeds a threshold value;
setting the first content encryption key as an inactive encryption key for the asset cluster;
generating, for the asset cluster and based on the master encryption key for the asset cluster, a second content encryption key;
setting the second content encryption key as the active encryption key for the asset cluster;
for a second subset of the plurality of data items in the asset cluster, encrypting the second subset of the plurality of data items using the active encryption key and maintaining a second count of the number of data items encrypted using the active encryption key;
based on generating the second content encryption key, decrypting, using the first content encryption key that is set as the inactive encryption key, each of the first subset of the plurality of data items for the asset cluster; and
encrypting, using the active encryption key, each of the first subset of the plurality of data items for the asset cluster.
|