| CPC H04L 63/1433 (2013.01) [G06F 9/45558 (2013.01); G06F 9/5072 (2013.01); G06F 21/54 (2013.01); G06F 21/554 (2013.01); G06F 21/568 (2013.01); G06F 21/577 (2013.01); G06F 21/78 (2013.01); H04L 9/0825 (2013.01); H04L 9/0894 (2013.01); H04L 9/14 (2013.01); H04L 63/10 (2013.01); H04L 63/1441 (2013.01); H04L 63/145 (2013.01); H04L 67/1008 (2013.01); H04L 67/101 (2013.01); G06F 2009/4557 (2013.01); G06F 2009/45595 (2013.01); G06F 2221/034 (2013.01)] | 18 Claims |
|
1. A cyber security system for a cloud environment, the system comprising:
at least one hardware processor configured to:
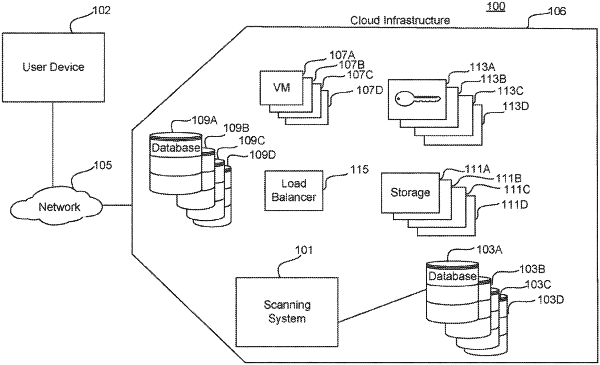
cause a target account in a target system of a cloud storage environment to authorize access privileges to an account on a scanning system via a cloud provider API to enable the scanning system to access a block storage volume of a workload maintained on the target account;
utilize the scanning system at a location of the block storage volume and on a secondary system other than the target system to scan the block storage volume for malicious code, wherein utilizing the scanner includes modifying a pre-utilized scanner at the location of the block storage volume based on information related to the target account to obtain a modified scanner, and utilizing the modified scanner;
identify malicious code based on the scan; and
output from the secondary system, a notification of a presence of malicious code in the target system.
|