| CPC H04L 63/1433 (2013.01) [H04L 63/0236 (2013.01); H04L 63/0884 (2013.01)] | 20 Claims |
|
1. A testing device comprising:
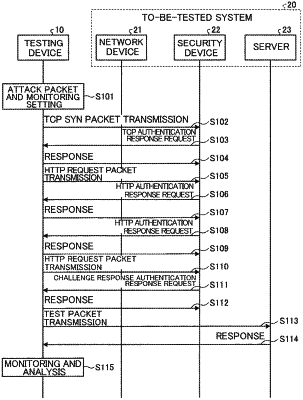
a transmitter configured to transmit a test packet that increases processing load to a device protected by a security system, the security system performing authentication of a packet transmitted to a to-be-protected device and a packet limit per source IP address;
a test scenario generator configured to generate a test session according to a scenario when transmitting the test packet;
an address distributor configured to configure a packet so that the test packet uses a plurality of source IP addresses;
a responder configured to respond to response requests up to a predetermined stage of authentication among a plurality of stages of authentication performed by the security system so that the security system authenticates the test packet to be valid;
a surveillance monitor configured to monitor, at the predetermined stage, packet filtering situation and processing load of the security system to which the test packet is transmitted;
wherein the surveillance monitor monitors the packet filtering situation based at least on the number of test packets, the byte amount, and the number of sessions per unit of time per source IP address, and whether there is a response packet from a to-be-test device; and
wherein the surveillance monitoring identifies a relevant source IP address that receives no response packet although other source IP address test packets receive a response packet and records the source IP address that receives no response packet, the number of test packets, the byte amount, the number of sessions, and a time stamp that are transmitted.
|